ICS의 탐지구조를 단계화(단순분석+복합분석)하여
False Positive를 최소화 하였고, 침입 공격 유형별로 분류되었고 CVE(Common Vulnerabilities
and Exposures)를 지원한다.
▶ 커널기반의 탐지엔진
ICS의 탐지엔진은 커널계층에서 동작하기 때문에
패킷을 처리하는데 소요되는 시간을 최소화하여 대용량 네트워크에서도 성능저하가 발생하지 않는다.
Passive 방식의 침입탐지시스템(NIDS)은 "패킷수집(Capture) --> 데이터축약
--> 분석 --> 판정"의
처리과정을 거치게 되지만, ICS는 "패킷수집", "데이터축약" 처리과정이
대폭 생략되었기 때문에 대용량 트래픽 분석이 가능하다.
또한 패킷의 상태분석(Stateful Inspection)기법을 사용하여 중복 분석 및 False Positive를 최소화
하였다.
▶ Active-active High Availability
별도의 Load-balancer(L4 Switch)에
의한 Active-active 방식의 고가용성을 지원하여
Single point of failure에 대응할 수 있다.
(차기 버전에서 자체 Active-active 고가용성을 지원할 계획임)
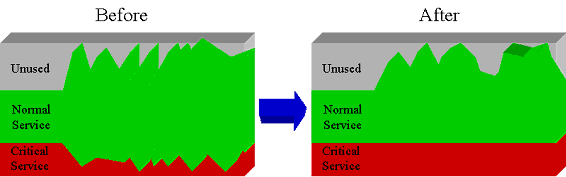
▶ 네트워크 대역폭 계획 조정(Traffic Shaping)
ICS의 통제엔진은 허용된 규칙에 대해 Traffic
Shaping이 가능하여 DoS(DDoS) 공격에 의한 네트워크 자원 소모를 원천적으로 통제할 수 있을 뿐 아니라 중요한
서비스에 대해 일정한 네트워크 대역폭(Bandwidth)을 할당하여 안정적인 서비스가 가능하다.
▶Traffic Shaping 예제
|
